Need for Security
- To only permit authorised users to access what they need
- To prevent unauthorised access
- To minimise potential damage from unauthorised access
Firewall
- Controls access to and from a network
- Manages which ports are open, permitting only certain traffic to pass through
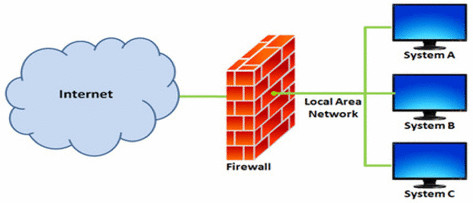
Packet Filtering
- Identifies ports accessed by packets, i.e., 80 (commonly used for HTTP traffic)
- If permitted, the port must remain open for the entire duration of the connection
Proxy Server
‘Proxy’ means ‘on behalf of’
- Traffics network communications
- The ‘true’ IP is not publicly sent in requests
Functions
- Enables anonymous internet browsing
- Can be used to filter undesirable content
- Can be used to log user requests
- Provides caching
Encryption
- Network traffic could be encrypted, i.e., plaintext messages, communication between a the user and the proxy
Monitoring
- Monitoring what is occurring within a network and keeping logs
- Packet sniffers
- User access logs
Prevention
- Up-to-date software (patches, reduce vulnerabilities)
- Up-to-date anti-malware